- Dive deeper into common advertising fraud types and learn about new, lesser-known ad frauds that often go unnoticed.
- Discover how these new advertising frauds occur and their impact on ad spending.
In our last episode we discussed ‘What Advertising Fraud Looks Like Today’ and how it prevents advertisers from making the right campaign decisions, eventually leading to a negative ROI.
If you missed the previous episode, you will be able to access it here. To build a layered perspective on the types of advertising fraud we discussed earlier, we will go a step further by taking you through how to spot them. Let’s begin!
WHAT IS CLICK HIJACKING?
Click hijacking is a common form of attribution fraud where fake clicks are sent just after the app install begins, tricking attribution tools into crediting the wrong source. Luckily this is relatively straightforward to monitor and detect.
HOW TO SPOT CLICK HIJACKING?
If there is a significantly short time between the click and app install it is a strong indicator of Click Hijacking. Below is an example of the time distribution of Click To Install Time (CTIT) difference observed for an ad campaign.
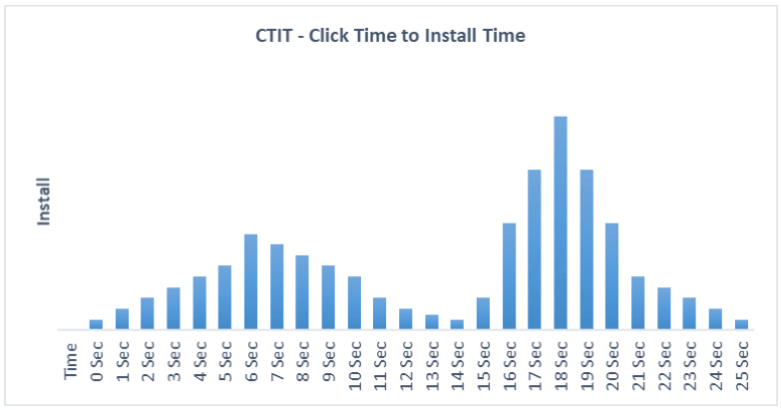
For Example: In this chart, the volume of installs recorded with CTIT (mean click to install time) that is less than 15 seconds is quite high. Therefore, the likelihood of click hijacking being a factor increases. This is simply because it isn’t practically possible for a network to process the app store action at such high speeds.
Disclaimer: This type of advertising fraud only occurs in an android environment as iOS limits app tracking as per new user policy and data use.
WHAT IS SPAMMING?
Spamming occurs when fraudsters send a large number of fraudulent clicks with the aim of hijacking the attribution for other publishers’ events.
HOW TO SPOT SPAMMING?
Spamming can be identified if there is a high volume of clicks (usually in thousands or millions) resulting in a minimal number of installs and low conversion rates. this is a strong indicator of spamming fraud.
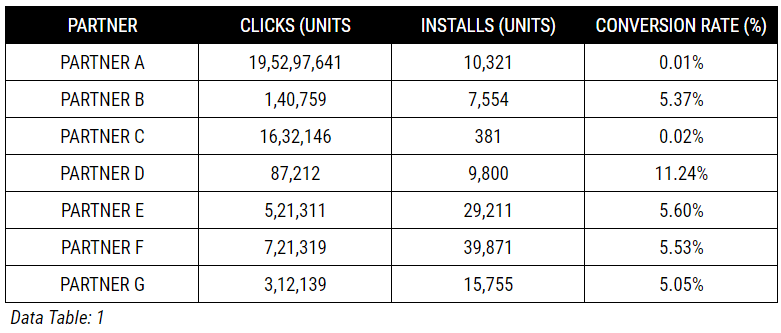
For example, in this sample campaign metrics table, Partner A has the lowest click-to-install ratio, but the highest number of clicks, which doesn’t align with the campaign benchmarks of 0.05% or less.
In contrast, Partner B’s event ratio appears normal when compared to campaign benchmarks for a banner ad campaign.
These anomalies can be found at the partner’s SiteID level clearly identifying the sub publishers that are the source of the spam.
WHAT IS GEO FRAUD?
Geo fraud occurs when events are triggered from locations outside the ad campaign’s targeted regions, typically exceeding a 3-5% threshold.
HOW TO SPOT GEO FRAUD?
Detecting geo fraud is relatively straightforward. When events from outside the campaign’s targeted regions exceed a certain percentage, it’s a strong indicator of Geo Fraud.
WHAT IS AN OUT-OF-STORE EVENT?
These are downloads of an outdated app version, compared to the latest version of the app on the Google Play Store.
HOW TO SPOT OUT-OF-STORE EVENT FRAUD?
Identifying this type of advertising fraud is challenging, especially in markets with high Android usage. Before we jump into the details, it will be important to learn about APK’s. APK (Android Package Kit) is a file format or extension used by android operating systems, allowing easy transfer and installation on Android devices. Android OS has a security protocol that requires user consent to install APKs from unknown sources.
Why do we need an APK? APKs are mainly used by Android developers to package their applications before uploading to the Google Play Store. Alternative app stores, such as Xiaomi Get Apps, Samsung Store, and Oppo App Store, use a similar method to install APKs on Android devices.
Typically, when a user clicks a banner ad, they’re directed to the Google Play Store. However, some device manufacturers have their own app stores, and users must choose which store to install the app from. Apps on the Google Play Store are frequently updated, while third-party app stores might not update apps as often.
When a user installs an app from a third-party app store, they may not get the latest version. This makes it difficult to determine if the app install came from a legitimate third-party app store or was the result of fraud.
Disclaimer: This type of advertising fraud only occurs in an android environment as iOS doesn’t support APK installation.
WHAT IS AD STACKING?
Ad stacking as the name suggests occurs when fraudsters layer multiple ads on top of each other. Multiple Impressions or clicks (or both) are sent to endpoints, even if users never interacted with the ads..
HOW TO SPOT AD STACKING?
Ad stacking can be identified by examining the average time between an ad impression and a user click. The shorter the time duration, the higher the likelihood of ad stacking. These fake impressions distort campaign data and create the impression that ad creatives are underperforming with a lower ROI.
One of the more advanced forms of advertising fraud that has emerged in recent times is SDK Spoofing. Let’s dive into what it is, how it works and how to spot it?
WHAT IS SDK SPOOFING?
SDK stands for Software Development Kit, which is used to create and run programs for an application. SDK Spoofing occurs when fraudsters manipulate data to present false events that never actually occurred. This form of fraud is referred to as a Man-In-The-Middle (MITM) attack, where information exchanged between users and an application is altered to appear genuine. Examples of MITM attacks include IP Spoofing, Cookie Hijacking, and Wi-Fi Eavesdropping.
HOW TO SPOT SDK SPOOFING?
SDK Spoofing can be detected by recognizing patterns of numerous fake clicks alongside fraudulent events such as app installs or in-app purchases. These fraud schemes are often highly sophisticated and can be executed without the knowledge of developers or app owners.
As we have delved into advanced technical advertising fraud, it’s essential to consider some cases that may go unnoticed due to their relatively low impact on ad spends.Such advertising frauds can jeopardise user data privacy and result in data alterations. Addressing these frauds may require collaboration from cross-functional teams or channel partners.
FINANCE FRAUD
Fraudsters gain unauthorised access to a user’s device to alter or misuse seemingly insignificant data. These small-scale attacks can accumulate and generate fraudulent transaction events on applications or websites.
DATA TAMPERING/ MANIPULATION
This type of fraud involves tampering with a system’s information, often just before processing, to distort data analytics. Fraudsters may alter key data and then revert it after processing or leave it unchanged.
In addition to technical advertising fraud, it’s important to recognize situations that might be misinterpreted as advertising fraud due to negligence or human error. These instances often occur when campaign frameworks or guidelines for protecting marketing investments are not followed. Some examples include:
GEO DISCREPANCY
Incorrect geo-targeting during setup or IP database mismatches between systems can cause discrepancies at country or regional levels. Unless a significant amount of data is found dubious, such errors could be misconstrued as advertising fraud.
COMPLIANCE FRAUD
This type of fraud results from human errors or negligence in following guidelines or requirements.
THIRD PARTY APP STORE INSTALLS
Targeting mobile manufacturers with preloaded third-party App Stores may lead users to download outdated app versions.
PROBABILISTIC BENCHMARKS
Using incorrect benchmarks on fraud tools during setup can result in genuine events being falsely identified as fraudulent.
KEY TAKEAWAYS
In this article, we learnt:
- Types of common technical advertising fraud and how to spot them: (Click Hijacking, Spamming, Geo Fraud, Out Of Store Event, Ad Stacking)
- Less common advanced technical advertising fraud such as SDK spoofing: how it works and how to spot it
- Extensions to advance technical Advertising Fraud (Finance Fraud, Data Tampering/ Manipulation)
- Misleading scenarios due to human negligence (Geo Discrepancy, Compliance Fraud, Third Party App Store Installs, Probabilistic Benchmarks)
WORKING WITH M&C SAATCHI PERFORMANCE
At M&C Saatchi Performance, we’ve a thorough understanding of the performance marketing ecosystem. We have established a robust fraud prevention methodology to minimise the impact of advertising frauds on our clients’ advertising spends.
Reach out to us to know more about our performance marketing services.
COMING UP IN OUR AD FRAUD SERIES
EPISODE #3: HOW TO TACKLE FRAUD
- Explore various fraud detection mechanisms, from simple methods to advanced tech tools, and learn about the role played by agencies like M&C Saatchi Performance in detecting and preventing advertising fraud.
EPISODE #4: HOW TO MAINTAIN A LOW FRAUD LEVEL LONG TERM
- Review methods of fraud prevention and discuss the use of benchmarks, optimisation techniques, and checkpoints to keep advertising fraud levels low over the long term.